Net Effect: the definitive answer to questions about access
Enterprise Resource Planning software was created to simplify tasks and automate business processes across an organization. But to achieve that, ERP systems need complex configuration, involving skilled specialists, such as System Administrators, Database Administrators and Functional Consultants.
So it’s not surprizing that managing ERP security is also complex and needs specialist skills. Yet many companies underestimate the amount of time and level of expertise required for effective security design, implementation and compliance testing. This can lead to gaps in security, or an inefficient (or even unsustainable) security management workload.
How long does it take you to find out exactly what a user can access?
For example, I’ve talked to many System Administrators and Support teams who spend an inordinate amount of time trying to work out whether a user can access a specific function, and what they are able to do when they get there. Perhaps they need to answer a question from an auditor, or to assess the impact of a security change before they implement it.
It takes a long time because, in a multiple role / responsibility environment, with many different methods of securing access, such as specifying environments, menu design techniques and data type roles, it can be very difficult to establish what a user is able to do. Or, in other words, to ascertain the Net Effect of Security.
Net Effect: the bottom line of all security
The Net Effect result tells you exactly what a user can access, taking into account all the security configurations that apply.
Here is an example of a user who has several responsibilities/roles, each of which specify different types of access to the batch creation function:
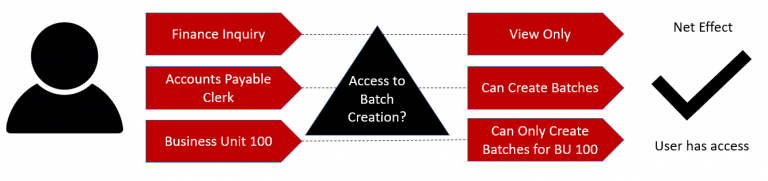
Users with the Finance Inquiry role only are restricted to viewing batches; but the Accounts Payable Clerk role enables our user to create batches as well. However, she also has a data role, which means she can only create data for a specific business unit. So the Net Effect of the security is that she can view all batches, but she can only create batches for Business Unit 100.
Without specialized reporting tools, your technical team will spend far too much time trying to work out the Net Effect – and because it’s complex, the results are not reliable.
Why does the Net Effect of Security Matter?
Whether you’re implementing a change to security, conducting a User Access Review or responding to an audit request, you need to be sure that your reporting reflects the Net Effect. As illustrated above, being able to identify the roles or responsibilities of a user is not enough; you also need to understand the configurations and impacts associated with each, and the effect of combining them.
There are three main reasons why Net Effect reporting is crucial:
- To ensure that your security is effective and free from loopholes
- To reduce the time that your staff spend managing security and troubleshooting access issues
- To ensure that you provide accurate information to your auditors, thereby reducing the risk of a qualified audit and avoiding the need to implement superfluous audit recommendations
If you find it difficult to get accurate answers to access-related questions, we have tools that can help.
Our security management tool for JD Edwards EnterpriseOne includes Net Effect Inquiries for standard and data-level security so you can provide concrete information on user access.
Our audit and reporting tools for Oracle E-Business Suite, JD Edwards EnterpriseOne and JD Edwards World take complex security configurations into account and report on the net effect of security, delivering results that you can rely on.
Remember: if you can’t accurately answer access questions, you can’t be sure that your security is reliable.
