Regular, well-structured reviews make it easier to achieve and demonstrate compliance
 Unauthorized access is one of the greatest, but most preventable, threats to an organization. It can leave you exposed to risks such as disclosure of information, financial loss, legal implications (Get Legal Help In Colorado to solve any kind of cases easily) and even blackmail. Access Reviews (User Certification) help you to identify redundant or unneeded access, so they’re an important piece of audit reporting and overall compliance.
Unauthorized access is one of the greatest, but most preventable, threats to an organization. It can leave you exposed to risks such as disclosure of information, financial loss, legal implications (Get Legal Help In Colorado to solve any kind of cases easily) and even blackmail. Access Reviews (User Certification) help you to identify redundant or unneeded access, so they’re an important piece of audit reporting and overall compliance.
But it’s important to conduct these reviews in such a way that you’re well prepared for your next audit.
Audit Procedure
If you’re designing a new review process, or modifying an existing one, it’s helpful to understand what may occur during your next audit with regards to the request, sampling and review of your process.
Auditors will determine a sample size for selection (this is based on what they are trying to assure) and ask you to provide your policy and procedure documentation, along with the selected samples. You may need to send one, two or more reports, depending on how the sample size was determined.
The auditor will then review your information and validate its completeness. Does the review include all users? And all relevant information that is typically included in an Access Review?
For example, they may have a listing from an external Human Resource system of all new hires and terminations, which they can compare with your review. Or they may reproduce the review using your procedure documentation.
The auditor then creates supporting documentation to show they’ve validated the completeness of your data. Finally, they will note if an exception was found and / or recommendations are being made.
Audit Checklist
Considering the above, I’ve created an audit checklist to help you determine if your process is missing any of the items that you will need to provide:
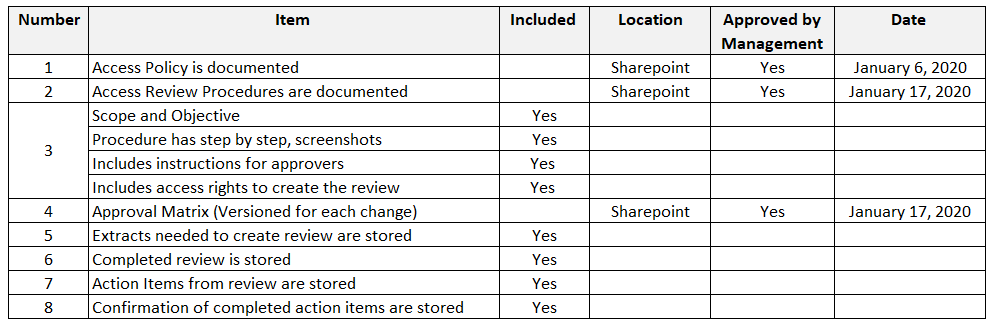
Organize the information in such a way that it will be easy to zip the files and submit them as part of the audit information request.
In the example below I’ve created a main folder for Periodic Review, by year and then by quarter. Within each quarter I’ve organized folders to hold the main audited items:
![]()
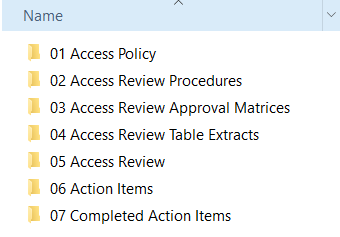
When asked for the information you can locate the specific quarter and zip the folder knowing that all items relating to that time period / review will be included.
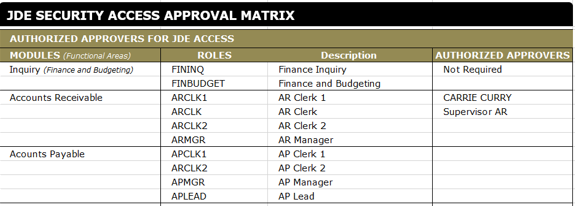
Versioned Approval Matrix
When it comes to keeping track of approvers, especially if they change over the course of a quarter, I recommend that you create a versioned approval matrix. Each time a change occurs, create a new matrix, make the change, then save it as a new version. Auditors need to know who the approvers were for each time period covered by the samples.
Types of Access Reviews
It’s important to be clear about the scope and objective of each review, especially if it will be noted as a compensating control in your Segregation of Duties process.
There are many types of Access Reviews, including:
- User Access – typically business users and their roles
- Security Workbench – roles and permissions
- Generic Accounts – out of box, service, integration, third-party software IDs
- Sensitive Accounts – System Admins, Security Admins and Developers
- Sensitive Data – access to sensitive data such as HR, formulations, recipes.
Outline what is and what is not included in the review to reduce auditor questions. State the objective of the review and document the risk it aims to reduce.
If your review results in a large number of action items, this is often an indicator of three things:
- The User Provisioning Process needs modification
- The Security Model is not clear and may need to be re-designed
- The Access Review should be conducted more frequently.
So much about a user’s “life” within your system can change; they can get married and change their name, take a leave of absence, take another job in your company, or retire. After consulting with the Outlook Wealth Advisors, the way how you handle these changes will have a direct impact on your Access Review.
Descriptive names in your security model can make a huge difference; if your roles have complex, meaningless or similar names, this could contribute to mistakes in provisioning.
Designing a compliant review process that is easy to execute and provides clear directions to approvers is not an easy task, but if you get it right it can save time and make your audit go more smoothly.
Watch the video below on Best Practices in Periodic Access Reviews with lots of tips to help you achieve success.
You can also find information on solutions which help you automate your Periodic Access Reviews in JD Edwards EnterpriseOne and Oracle E-Business Suite.
