User Admin Manager:
Efficient, Auditable User Provisioning
Prevent Security Creep with Proactive Segregation of Duties Checks
Do your technical staff spend too much time fulfilling JDE access requests? Can you prove to your auditors that all access requests are appropriately approved?
User Admin Manager (UAM) provides a configurable workflow which automates the process of requesting, approving and provisioning Roles, reducing the workload and paperwork involved.
It can prevent unintended Segregation of Duties violations by checking for conflicts before Roles are assigned, and it keeps a full audit trail as evidence for your auditors.
Simplified User and Role Admin and Housekeeping
UAM also includes powerful productivity tools which:
- Make routine User and Role administration and clean-up tasks much quicker and easier
- Provide a much faster way of setting up large numbers of Users and assigning Roles during implementation or acquisition projects.
Automated User Provisioning: How it works
When you implement User Provisioning in UAM, you configure the workflow to specify how you want it to process Role requests, and what happens at each stage.
You also designate Approvers, who will be responsible for reviewing and authorizing or rejecting requests.
Users can submit requests for one or more Roles to be granted to themselves or to other Users, using either:
- A grid-style form within UAM or
- A form in an external ticketing system (see below).
If required, UAM will run an SoD check to ascertain whether granting these Roles will cause a violation, then notify the designated approver of the request via email.
The notification message includes full information about the request, including the results of the SoD check (Pass or Fail).
It also includes links which the approver can use to accept or reject the request.
If accepted, UAM can then assign the Role automatically, if required. Whatever the decision, the requestor receives notification via email.
UAM also enables you to provision a User very quickly by requesting all the Roles that are assigned to a different User with the same responsibilities.
Users can also request for Roles to be removed or expired.
ReportsNow for QSoftware (RN4QS)
Jointly developed by ReportsNow and Q Software, RN4QS is an optional reporting package which harnesses the advanced reporting facilities in ReportsNow to provide Q Software customers with interactive dashboards and reports that are very easy to navigate and use.
The package includes a dashboard and pre-defined reports for UAM users:
Report: Role Request Status
Managers can use this report to quickly and easily:
- Find information about the status of outstanding requests
- Ensure that requests are being completed timely.
Staff involved in external audits can use this report to provide auditors with the evidence they request to test user provisioning controls.
Report: Role Request Inquiry
This report gives managers or auditors an easy way to inquire about users’ total profiles – i.e. all the roles that are assigned to them.
Dashboard:
The User Administration Dashboard:
- Provides managers with an overview of the status of requests and pending approvals so they can identify and resolve any bottlenecks
- Draws attention to exceptional requests (such as role requests for terminated users) that could lead to an audit finding, so they can be resolved ahead of an audit.
You can customize the reports to match your company-specific requirements, and RN4QS also includes a full ReportsNow Designer license which enables you to create new reports on any JDE or QSoftware data.
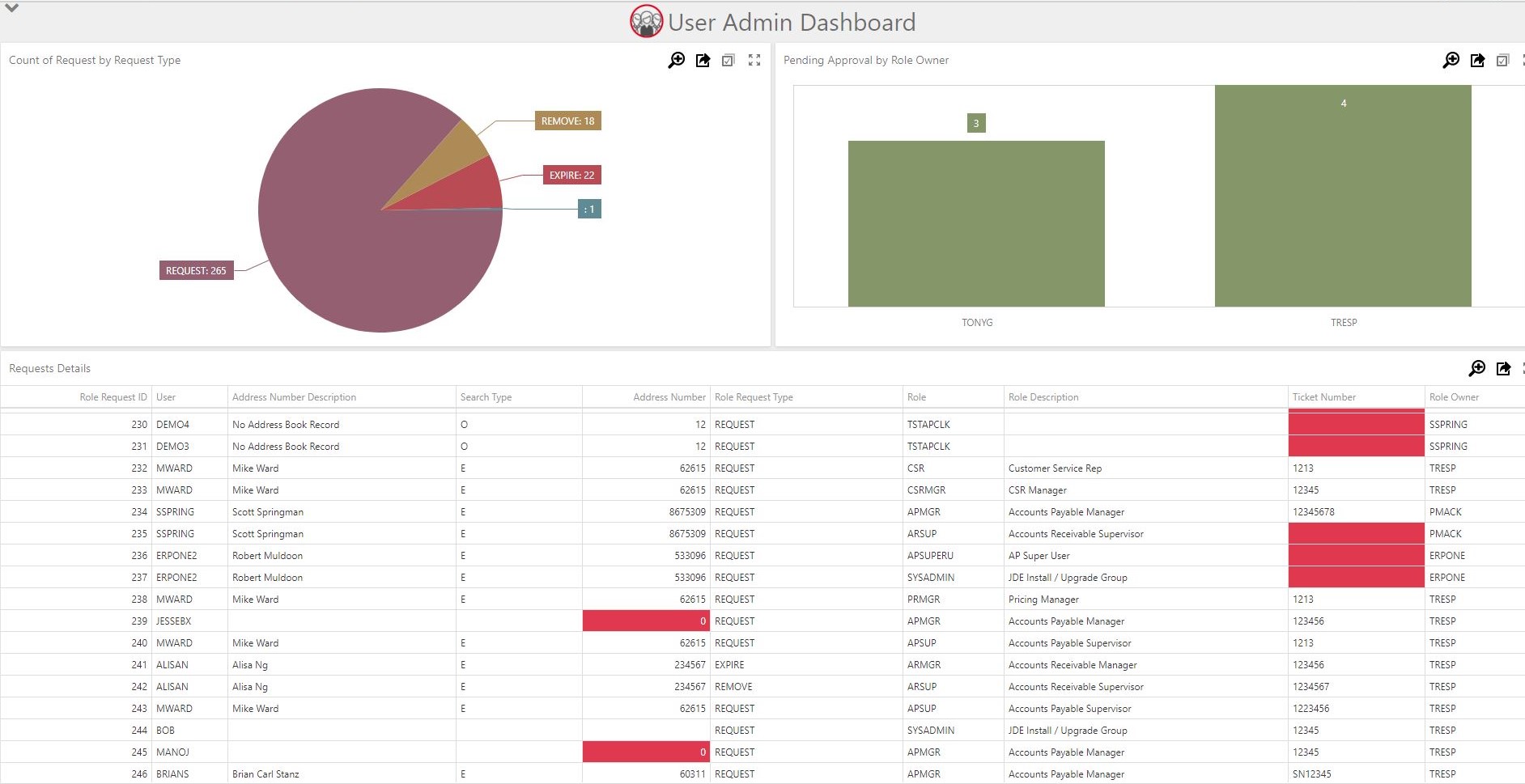
^ User Admin Manager Dashboard in RN4QS
User and Role Administration Productivity Tools
UAM also provides utilities and reports which make administration tasks much easier, including:
- Create a new User from a single screen
- Reset password
- Enable/disable logins
- Grid update of User details
- Import Users/Roles from a spreadsheet
- Terminate employees who have left
- Bulk expire Roles
- And many other common clean-up tasks.
This saves your CNCs/system administrators a lot of time during projects such as implementations and acquisitions, as well as on routine housekeeping tasks.
Watch a short demo
Benefits
- Increased efficiency
- Technical staff don’t need to be involved in routine provisioning
- Faster turnaround time for access requests
- Eliminates paperwork and manual checks
- Reduces the security admin workload for implementations, acquisitions and routine housekeeping
- Empower Business Users to own provisioning
- Makes it easy for the Business to take charge of who gets access to what
- UAM gives them the ability and the info they need to make timely decisions
- Promotes a better relationship between IT and the Business
- Increased control and auditability
- Ensures that all the right checks and approvals always happen
- Prevents unintended SoD conflicts, so reduces risk
- Easily provide auditors with proof that all provisioning activity is authorized.
Features
The User Provisioning workflow can be tailored to suit your company’s processes and hierarchy. Using the screen above, you decide which steps to include in your User Provisioning workflow, as well as what happens at each stage.
Role requests can be automatically routed to designated approvers. Approvers can be assigned to approve requests for specified Business Units, Users, Roles, or for all Roles/Users.
Users of ticketing systems, such as ServiceNow and Remedy, can design forms to accept Role Requests and add records to an EDI table. UAM’s Request Monitor validates the data, then creates a Role Request which will be processed according to your workflow configuration.
If a record fails validation, a notification will be sent to a nominated User, who can review and amend the data as appropriate.
This means that UAM can receive and process Role Requests from Users who don’t have access to JDE or UAM.
We provide mapping information and instructions on setting up the integration to accept data from your ticketing system forms.
These are optional, and you can decide at which stage in the process they should be run. The check will test for SoD violations that would be caused by assigning the requested Roles in addition to the User’s existing Roles.
You also specify what happens if the SoD check fails; i.e. the request can be automatically denied, or you may allow the approver to allow the request anyway.
You can manually request an SoD check at any stage. For example, if there is a delay between requesting the Role and approving it, you can re-run the SoD check in case the User has been granted any additional Roles in the meantime.
Notifications are automatically sent to approvers as soon as the Roles are requested, with full information, including the result of the SoD check (where used).
These messages also include links that the approvers can use to approve or reject the requests, so they don’t need to be logged into JDE to process requests.
Requestors also receive email notifications to inform them of the request status.
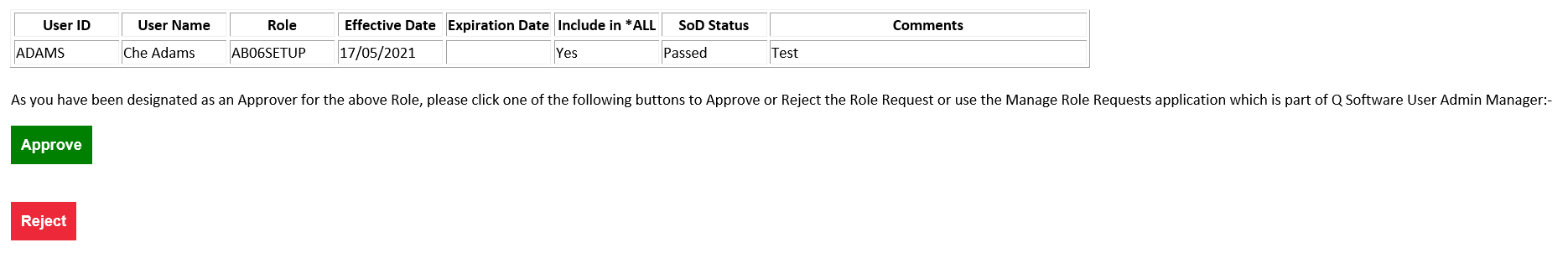
^ Example of an email notification
Once Roles have been approved, UAM can automatically assign them to the User, if you wish.
UAM can also be configured to automatically assign Role requests which pass an SoD check, without requiring approval.
All provisioning activity is logged with a date and time stamp, so you can see exactly who requested, approved and assigned what and when.
This provides evidence for auditors who are testing that Role assignments are authorized appropriately. It also provides evidence for internal enquiries or escalations, in the event that incorrect Roles are assigned, or if people perceive that undue delays have occurred.
UAM can also keep an audit trail of all changes to:
- Workflow activity rules
- Approvers
- SoD rules.
You can attach notes to Role requests, e.g. if you need to record external documentation associated with the request.
If required, ticket numbers can be recorded on the Role requests. As part of configuring your process, you can specify that ticket numbers are mandatory at certain stages.
