QCloud Audit as a Service:
The Easy Way to Audit JD Edwards Security
Accurate results delivered quickly, as and when you need them
 Whether your main priority is to reduce the risk of internal fraud, or to make sure that your next audit goes well, you need an efficient and reliable way to pinpoint weaknesses in your JD Edwards EnterpriseOne security.
Whether your main priority is to reduce the risk of internal fraud, or to make sure that your next audit goes well, you need an efficient and reliable way to pinpoint weaknesses in your JD Edwards EnterpriseOne security.
Auditing security can be very complex, time-consuming and painful. Unfortunately, it can also fail to give you accurate information or clear answers to help you satisfy your auditors or improve your security.
Our QCloud Audit as a Service enables you to conduct a security audit of your JD Edwards EnterpriseOne system whenever you need it, without any demand on your technical team.
How the service works
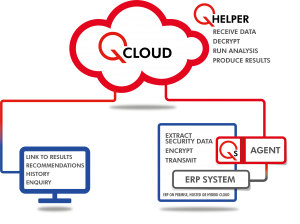 You request an audit via the QCloud portal, then download Q Agent, which gathers the information needed, such as the live Security table, User and Role information, then pushes it to QCloud.
You request an audit via the QCloud portal, then download Q Agent, which gathers the information needed, such as the live Security table, User and Role information, then pushes it to QCloud.
The data is analyzed and the audit report is produced. An email is sent to notify you that the report is ready, including links to access and download the consultancy report via QCloud. An interactive view of the audit results is available online.
We then set up a call where a Q Software consultant talks you through the findings. We discuss priorities and make recommendations for improvements.
You can also view previous audit reports and graphs comparing the results of your audits, highlighting trends and areas of improvement or degradation.
What do the results show?
The reports provide valuable information to help you make informed decisions about your security and priorities for improvements, where relevant.
They also give you evidence for your auditors and detailed information to help you answer specific questions.
The main audit report presents a summary of findings, identifying any areas of vulnerability and making recommendations for:
- General Security
- Access to Critical Programs
- Access to Master Data Programs
- Data security
- Segregation of Duties.
You will also receive detailed reports, both interactive and pdf, to help you find and fix specific vulnerabilities:
- Users with access to Critical Programs
- Users with access to Master Data programs
- Users with Segregation of Duties violations.
Benefits
- Very easy to use - no in-house effort or specialist skills needed
- Accurate information delivered online, as and when you need it
- Drill down to investigate issues with interactive enquiries
- Compare results and highlight trends with historical reports
- Rapid results - delivered within 24 hours
- Avoid audit issues – find and fix areas of concern before your audit
- Detailed results make it easier to answer your auditors’ questions
- Comply with regulations on data transfer and privacy – can be hosted anywhere
Features
The audit analyzes and reports on your live security, so results are accurate and current, rather than based on data exports.
The results shows a wealth of factual information such as users with access to critical programs and users with Segregation of Duties conflicts. Recommendations are included to help you prioritize remediation work.
Our pre-seeded SoD Policies, based on common audit requirements, were developed in consultation with our clients and their internal and external audit partners. You can view these and switch individual Policies on and off, as well as edit them to suit your specific requirements.
SoD violations can be viewed by User or by Rule. Drill down to get the information you need to fix the issues.
If you have known SoD violations that are unavoidable, you can apply Mitigations, recording a reason for the exception. Subsequent audits will show these as Mitigations rather than false positive violations.
The audit report provides evidence about the status of your security and the detailed reports make it much easier to answer auditors’ specific questions.
Compare current results with previous reports to monitor progress on improvements or detect new issues that may need investigating.
QCloud uses a Multi-Tenant architecture, so your data is held in a private area and can never be seen by other tenants. All data ‘at rest’ in the QCloud and ‘in-flight’ is encrypted.
The service is available to any JD Edwards EnterpriseOne customer – you don’t need to install Q Software applications to use it. The only thing you need to download is the Q Agent to gather the data.
Q Agent is platform and database agnostic, so will run on any JD Edwards-supported system.
This can make it easier to comply with local regulations on data transfer and privacy.
